- 前置工作
- 环境为 Centos 7 64位系统
- 检查系统是否安装了bindutil,检查方式为在命令行里输入 dig 看看是否提示图显示内容,此工具不是必须安装的,为了后续方便检查配置是否正确,还是建议安装一下
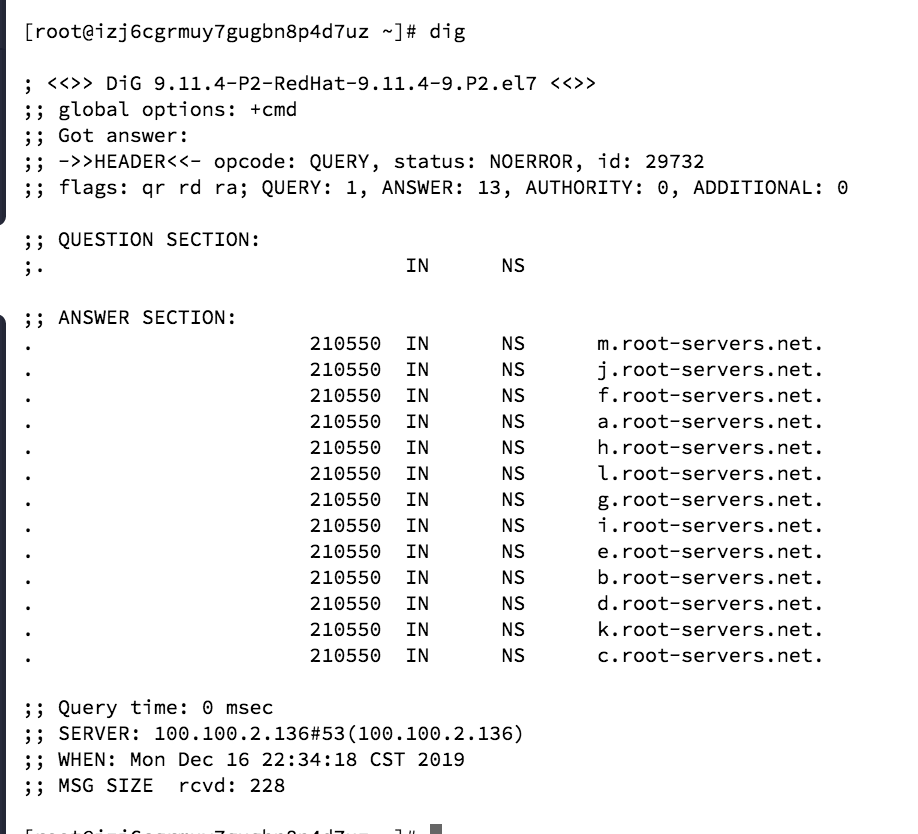
- 安装命令 :
yum install -y bind-util
- 申请证书
certbot certonly -d *.你的域名 --manual --preferred-challenges dns --server https://acme-v02.api.letsencrypt.org/directory
- 根据提示填写信息,到提示填写DNS解析的时候暂停一下,先去配置域名解析,如下提示
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Plugins selected: Authenticator manual, Installer None
Enter email address (used for urgent renewal and security notices) (Enter 'c' to
cancel): ljz1318078262@163.com
Starting new HTTPS connection (1): acme-v02.api.letsencrypt.org
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please read the Terms of Service at
https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must
agree in order to register with the ACME server at
https://acme-v02.api.letsencrypt.org/directory
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(A)gree/(C)ancel: A
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Would you be willing to share your email address with the Electronic Frontier
Foundation, a founding partner of the Let's Encrypt project and the non-profit
organization that develops Certbot? We'd like to send you email about our work
encrypting the web, EFF news, campaigns, and ways to support digital freedom.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: N
Obtaining a new certificate
Performing the following challenges:
dns-01 challenge for wzlinux.com
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
NOTE: The IP of this machine will be publicly logged as having requested this
certificate. If you're running certbot in manual mode on a machine that is not
your server, please ensure you're okay with that.
Are you OK with your IP being logged?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: Y
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please deploy a DNS TXT record under the name
_acme-challenge.wzlinux.com with the following value:
tgiYQeAxCxAO_f0Xjm3xUdAneGu3Ah_fhNzrVWXQ308
Before continuing, verify the record is deployed.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Press Enter to Continue
- 配置文件解析,我的域名是在阿里云管理的,以下为配置信息,记录值为命令行里提示的那个字符串
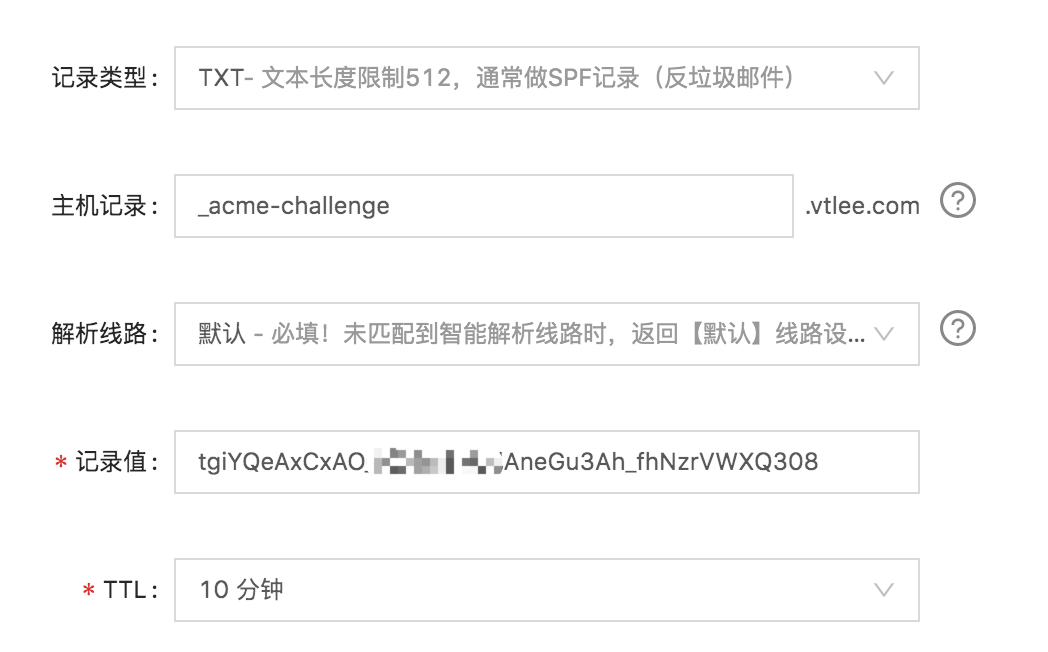
- 配置好之后,打开一个新的窗口,验证一下是否解析成功,在 ANSWER SECTION 中看到与上面暂停步骤一致的字符串,既是解析成功了,可以按回车继续一下步,程序会自动生成证书
[root@izj6cgrmuy7gugbn8p4d7uz ~]# dig -t txt _acme-challenge.vtlee.com
; <<>> DiG 9.11.4-P2-RedHat-9.11.4-9.P2.el7 <<>> -t txt _acme-challenge.vtlee.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 43443
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;_acme-challenge.vtlee.com. IN TXT
;; ANSWER SECTION:
_acme-challenge.vtlee.com. 600 IN TXT "tgiYQeAxCxAO_f0Xjm3xUdAneGu3Ah_fhNzrVWXQ308"
;; Query time: 16 msec
;; SERVER: 100.100.2.136#53(100.100.2.136)
;; WHEN: Wed Dec 18 08:17:59 CST 2019
;; MSG SIZE rcvd: 110
Waiting for verification...
Cleaning up challenges
Resetting dropped connection: acme-v02.api.letsencrypt.org
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/vtlee.com/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/vtlee.com/privkey.pem
Your cert will expire on 2019-09-04. To obtain a new or tweaked
version of this certificate in the future, simply run certbot
again. To non-interactively renew *all* of your certificates, run
"certbot renew"
- Your account credentials have been saved in your Certbot
configuration directory at /etc/letsencrypt. You should make a
secure backup of this folder now. This configuration directory will
also contain certificates and private keys obtained by Certbot so
making regular backups of this folder is ideal.
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
- 配置证书
[root@izj6cgrmuy7gugbn8p4d7uz ~]# ll /etc/letsencrypt/live/vtlee.com/
total 4
lrwxrwxrwx 1 root root 33 Dec 14 23:09 cert.pem -> ../../archive/vtlee.com/cert1.pem
lrwxrwxrwx 1 root root 34 Dec 14 23:09 chain.pem -> ../../archive/vtlee.com/chain1.pem
lrwxrwxrwx 1 root root 38 Dec 14 23:09 fullchain.pem -> ../../archive/vtlee.com/fullchain1.pem
lrwxrwxrwx 1 root root 36 Dec 14 23:09 privkey.pem -> ../../archive/vtlee.com/privkey1.pem
-rw-r--r-- 1 root root 692 Dec 14 23:09 README
- 配置nginx,注意需要将域名信息替换为自己的域名,另外我这里配置了反向代理,因为本机内运行了一个blog程序
# 定义转发
upstream blog {
server 127.0.0.1:8090;
}
# 定义http 自动跳转 https
server
{
listen 80;
#listen [::]:80;
server_name blog.vtlee.com;
access_log /tmp/blog.access.log main;
error_log /tmp/blog.error.log;
return 301 https://$host$request_uri;
}
# 配置证书等信息
server {
listen 443 ssl http2;
#listen [::]:443 ssl http2;
server_name blog.vtlee.com;
index index.html index.htm index.php default.html default.htm default.php;
root /usr/share/nginx/html/;
ssl on;
ssl_certificate /etc/letsencrypt/live/vtlee.com/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/vtlee.com/privkey.pem;
ssl_session_timeout 5m;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_prefer_server_ciphers on;
ssl_ciphers "EECDH+CHACHA20:EECDH+CHACHA20-draft:EECDH+AES128:RSA+AES128:EECDH+AES256:RSA+AES256:EECDH+3DES:RSA+3DES:!MD5";
ssl_session_cache builtin:1000 shared:SSL:10m;
# openssl dhparam -out /usr/local/nginx/ssl/dhparam.pem 2048
#ssl_dhparam /usr/local/nginx/ssl/dhparam.pem;
#error_page 404 /404.html;
# Deny access to PHP files in specific directory
#location ~ /(wp-content|uploads|wp-includes|images)/.*\.php$ { deny all; }
access_log /tmp/blog.access.log main;
error_log /tmp/blog.error.log;
location / {
proxy_redirect off;
proxy_set_header Host $host:$server_port;
proxy_set_header X-Forwarded-For $remote_addr;
client_max_body_size 20m;
client_body_buffer_size 128k;
proxy_connect_timeout 600;
proxy_send_timeout 600;
proxy_read_timeout 900;
proxy_buffer_size 4k;
proxy_buffers 4 32k;
proxy_busy_buffers_size 64k;
proxy_temp_file_write_size 64k;
proxy_pass http://blog;
}
}
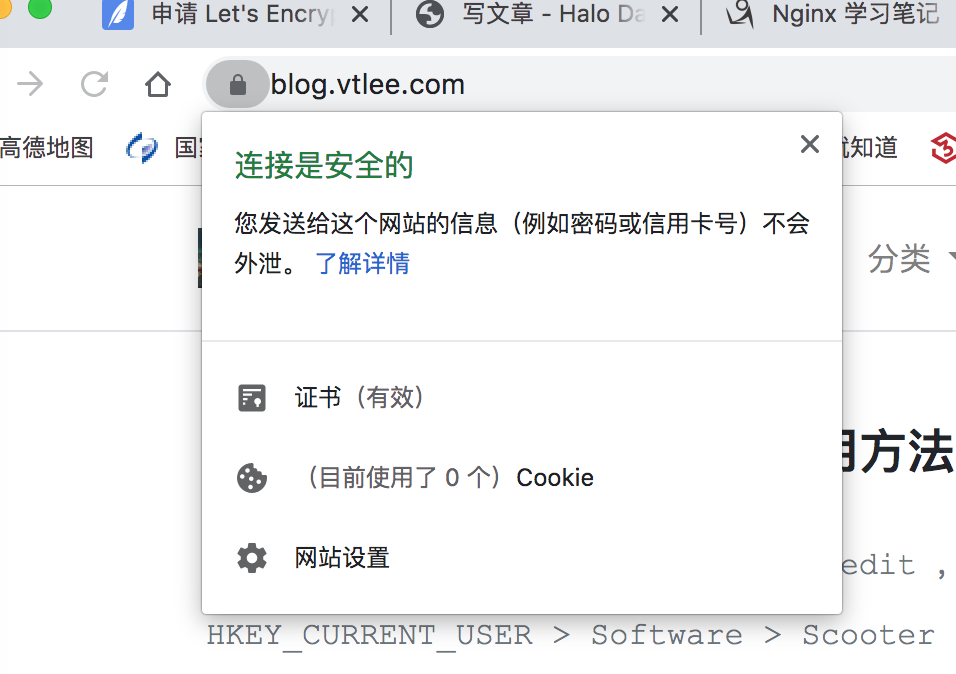
- 确认是否生效
- 打开浏览器,输入自己的网址信息,看看是不是如下图一样显示
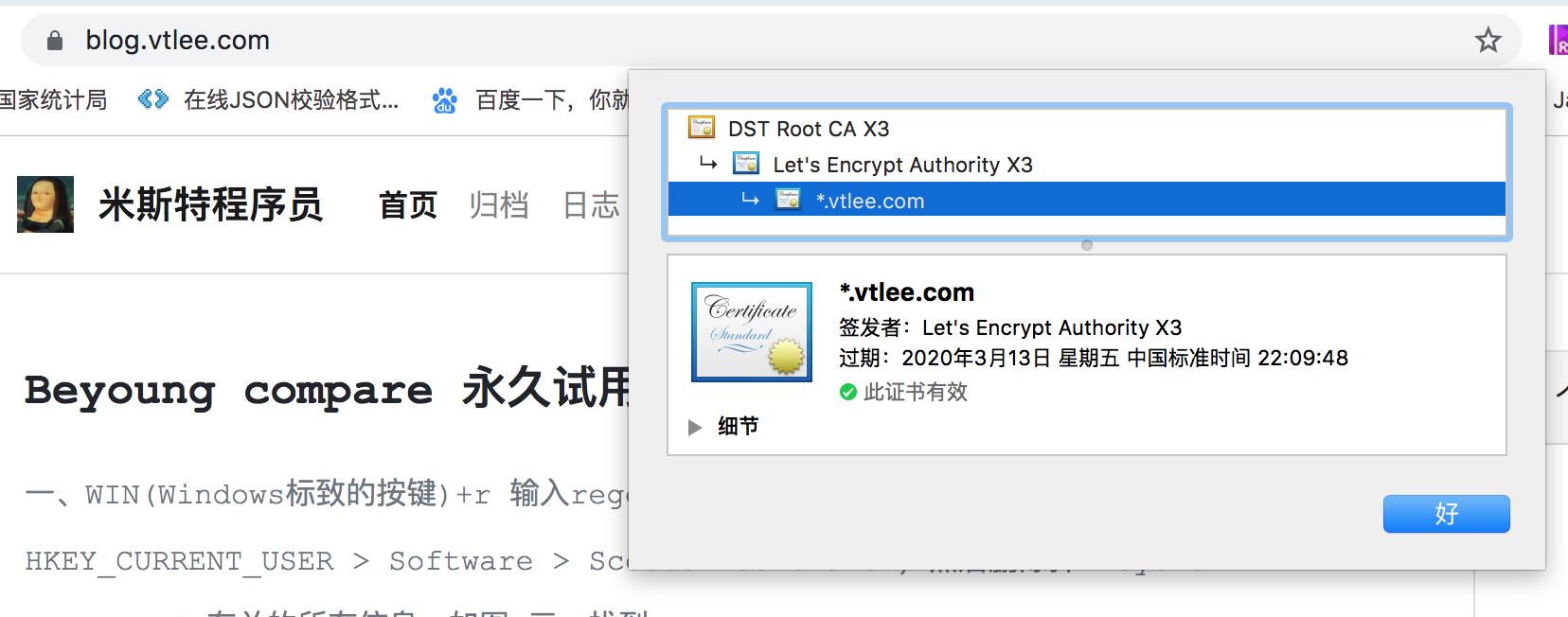
- 点击证书,看到如图显示信息
- 配置自动更新证书
0 59 23 L 1,3,5,7,9,11 ? /usr/bin/certbot renew && systemctl reload nginx.service
- 其它问题







